Press Release: Ashburn Consulting achieves AWS Select Tier Services Partner Status within the AWS Partner Network
Ashburn Consulting achieves AWS Select Tier Services Partner Status within the AWS Partner Network Tuesday, November 21st, 2023 – Ashburn Consulting LLC, renowned for providing top-tier IT cloud consulting services tailored to the unique needs of government and business sectors, announced today that they have achieved Amazon Web Services (AWS) Select Tier Services Partner status […]
ashburn,
November 29, 2023
The Dream Team of Cyber Security!
We are lined up amongst the big players in Cyber Security. Ashburn Consulting is a vendor agnostic Consulting Company. We recommend solutions that satisfies customer requirements aligned with their budget.
ashburn,
October 19, 2018
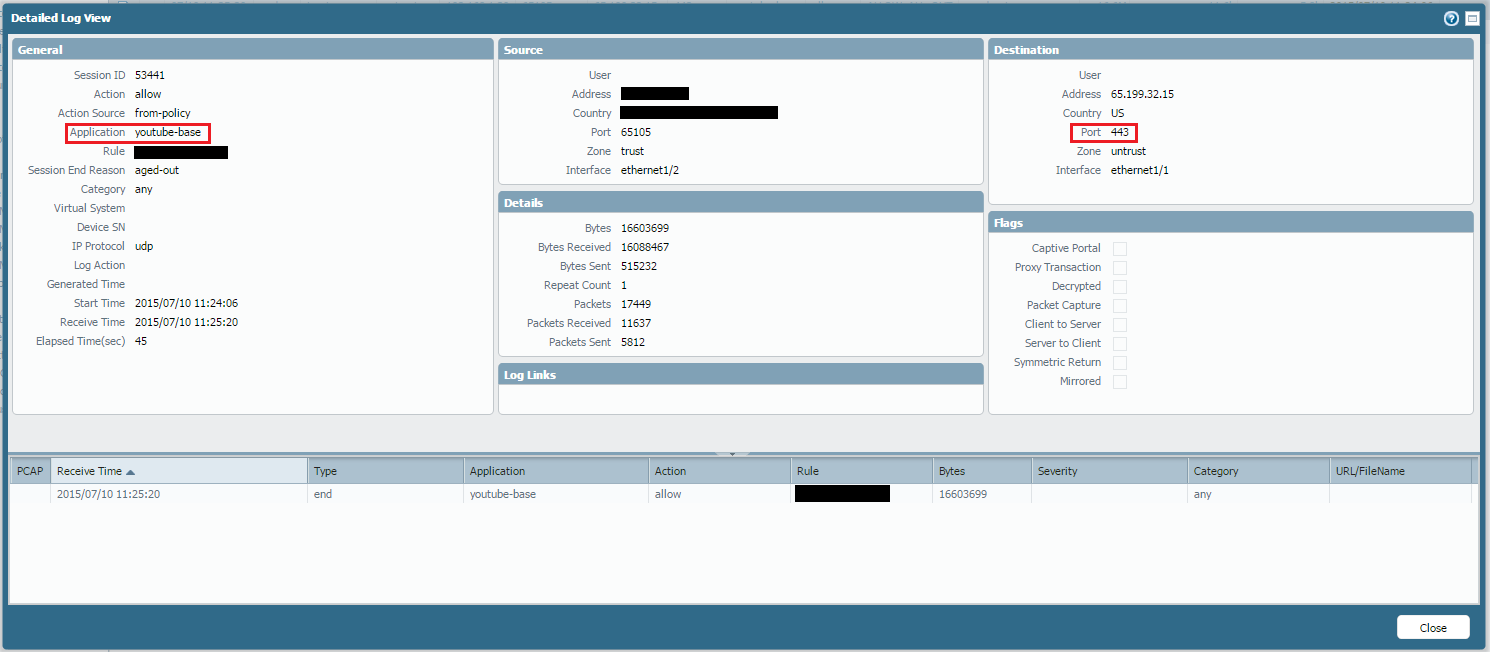
Next Generation Firewall Overview with Glimpse of Application Identification
“I am not an advocate for frequent changes in laws and constitutions, but laws and institutions must go hand in hand with the progress of the human mind. As that becomes more developed, more enlightened, as new discoveries are made, new truths discovered and manners and opinions change, with the change of circumstances, institutions must […]
ashburn,
July 11, 2015
ICMP Security
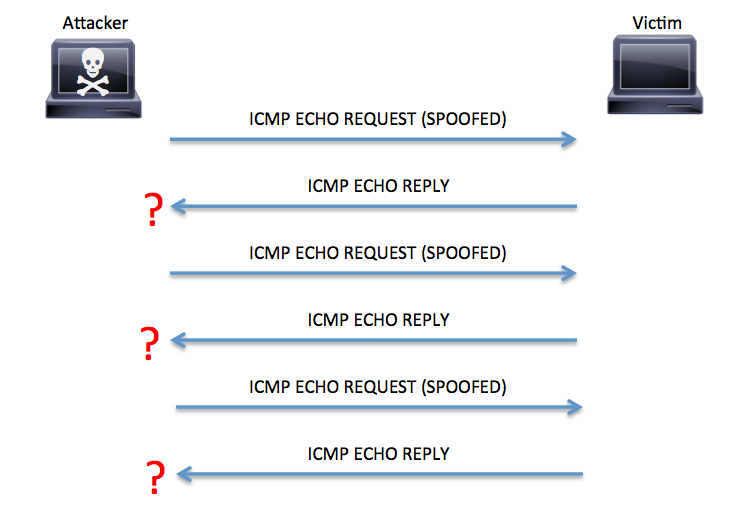
This is a draft guide to handling ICMP securely. Guide Analysis to Handling ICMP protocol Summary: This guide is an attempt to help answer common questions related to the handling of ICMP protocol in a secure and effective manner. Comments and feedback is always welcomed. This article is meant to cover the major area in […]
ashburn,
June 25, 2015
Layer 2 Tracing for (6500, 7609, 4500) Cisco Switches
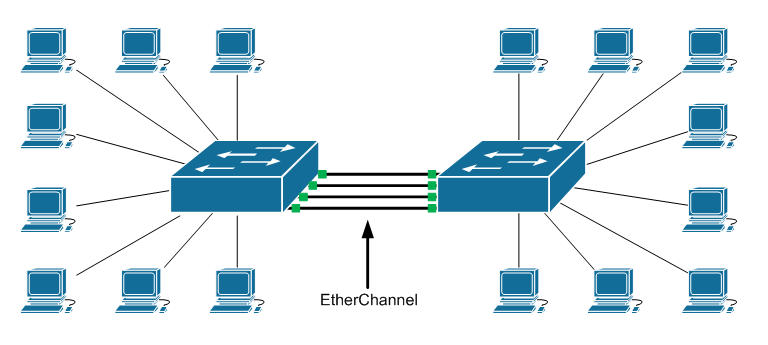
In a 6509, 7609 or any Chassis based Cisco switch, to determine where the switch forwards a Source and Destination pair to an actual port in a Port-channel/Etherchannel do the following commands: Note: Doesn’t apply to Nexus switches. First enter console for switch: port-channel hash Switch# remote login switch Trying Switch ... Entering CONSOLE for […]
ashburn,
June 25, 2015
MPLS L3 VPN White Paper
Enterprise Network Design White Paper For Metropolitan and Campus Networks – MPLS L3VPNs Robert Shields Sr. Network Engineer, CCIE # 12096 January 2012 Enterprise Network Challenges of Today and Beyond Enterprise network and security managers continue to see their responsibilities increase within their respective IT organizations as applications and services continue to migrate to IP as a fundamental means of communication. […]
ashburn,
September 27, 2014
INC 5000 list of fast growing Companies
[frame style=”modern” image_path=”http://www.simplesignal.com/blog/images/2013/08/inc-5000.jpg” link_to_page=”” target=”” float=”” lightbox=”#” lightbox_group=”” size=”three_col_large”] Ashburn Consulting has made the Inc. 5000 list of the fast growing companies in the nation! This is a tremendous accomplishment and I couldn’t be any more proud of each and every one of you that has made this a reality! We thank all of our […]
ashburn,
September 14, 2014
Press on Connect Arlington
Article about the new fiber network being built out in Arlington. Ashburn Consulting is the key Network Engineering contributor for making the project successful. Job well done by the Arlington team from Ashburn Consulting http://www.govtech.com/wireless/3-Reasons-Arlington-County-Started-Building-Fiber.html
ashburn,
September 14, 2014